Use a Yubikey remotely over RDP
Two factor authentication is great, but what about when you primarily do your work on a virtual desktop or need to sign in to a U2F application remotely? Luckily we can use RemoteFX USB device redirection to solve this problem and successfully authenticate using our local Yubikey on the remote machine.
It’s worth noting that this guide only applies to OTP/U2F functionality. You can use the native RDP smartcard redirection to use PIV and GPG functionality without doing any extra work.
Update 2020/12/30 - NO LONGER WORKING
It looks like a recent update or some change in browser behavior has caused U2F to no longer function properly over RemoteFX redirection. The device itself does redirect but the U2F functionality just times out in every browser I’ve tried. I’ll keep playing around with it but if you manage to get it working let me know!
Setting up the Client Machine
Updating the Local Group Policy
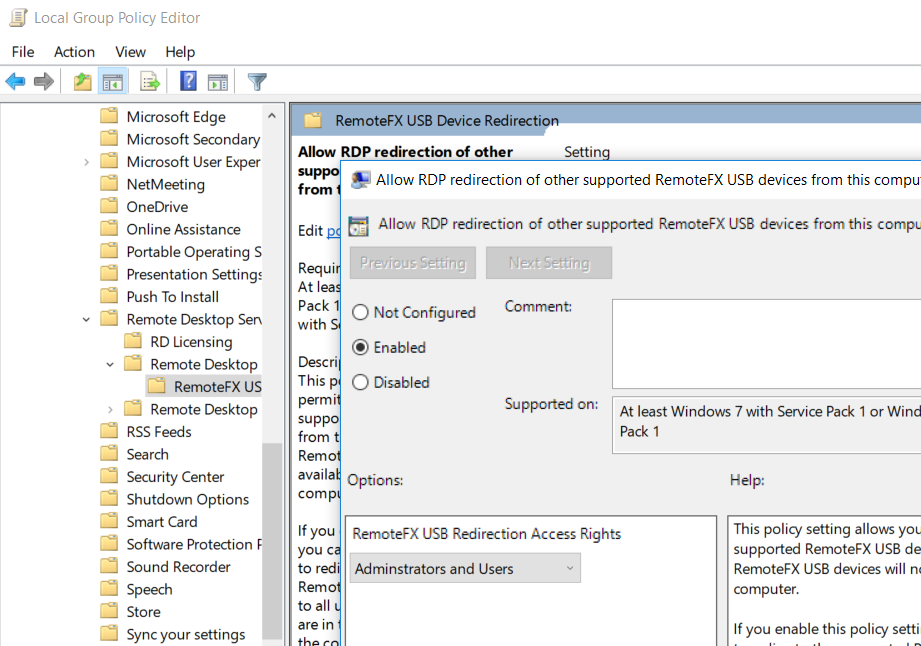 The first thing we’ll need to do on our client computer (the one where the Yubikey physically resides) is make some changes to Group Policy. You can do this via the “Local Group Policy” MMC or if you are domain-joined you can push out the setting with a domain Group Policy Object.
The first thing we’ll need to do on our client computer (the one where the Yubikey physically resides) is make some changes to Group Policy. You can do this via the “Local Group Policy” MMC or if you are domain-joined you can push out the setting with a domain Group Policy Object.
The policy we’re looking for is called “Allow RDP redirection of other supported RemoteFX USB devices from this computer” and is located here in the tree:
- Computer Configuration
- Administrative Templates
- Windows Components
- Remote Desktop Services
- Remote Desktop Connection Client
- RemoteFX USB Device Redirection
- Remote Desktop Connection Client
- Remote Desktop Services
- Windows Components
- Administrative Templates
Set the policy to “Enabled”. We can set it to either “Administrators and Users” or “Administrators Only” depending on the use-case.
Updating the Local Registry
We’ll also need to make some changes to the registry. By default Windows will not list the Yubikey as a device that can be redirected so we need to add it’s USB device ID to the list. I pulled these device IDs from a Yubikey 4 so your mileage may vary using other models. You can use the following registry file to automatically add the required entries.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services\Client\UsbSelectDeviceByInterfaces]
"Yubikey Smartcard"="{50dd5230-ba8a-11d1-bf5d-0000f805f530}"
"Yubikey FIDO"="{745a17a0-74d3-11d0-b6fe-00a0c90f57da}"
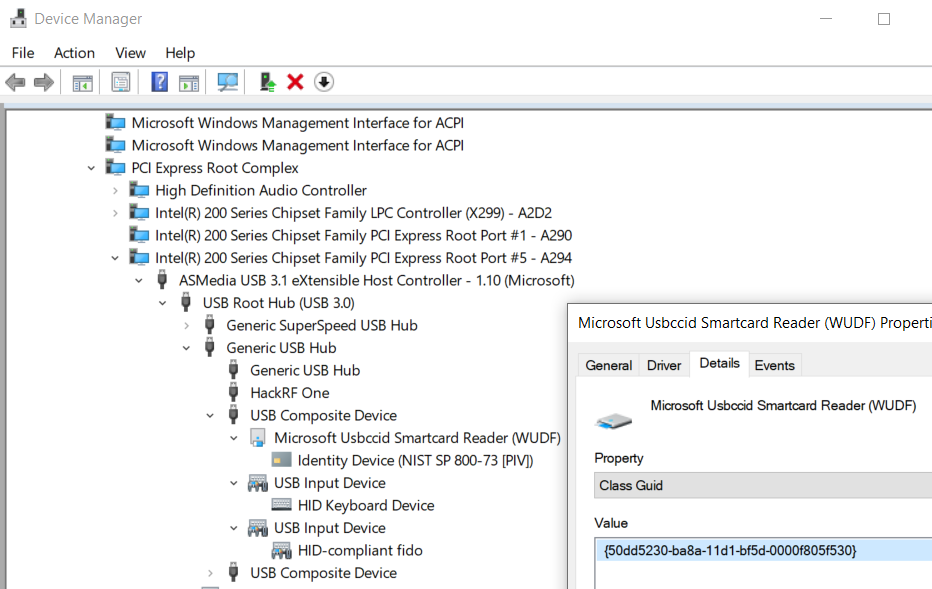
To find the ID for other models of Yubikey (or any other device for that matter) look at the “Class Guid” property of the top level device in Device Manger. The easiest way to find the YubiKey is to look under “Smart card readers”. You can find the HID device by switching to “Devices by connection” in the “View” menu and looking for the other entires under the same “USB Composite Device”.
After making these changes I recommend rebooting the client computer, although it may not be strictly necessary.
Setting up the Remote Machine
Updating the Remote Group Policy
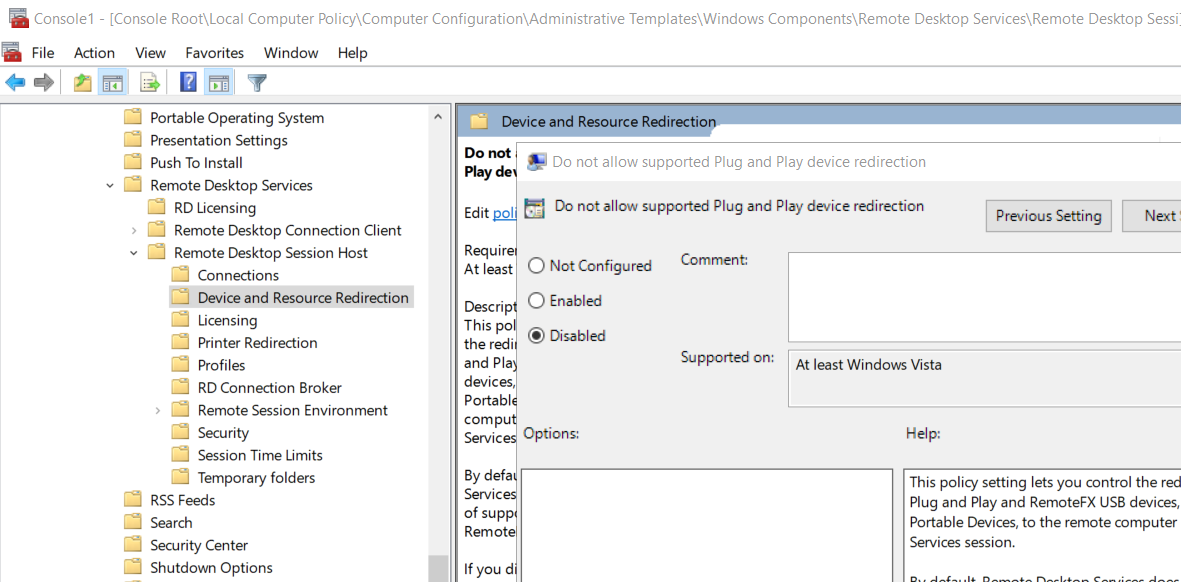
Similarly to the client computer we will need to update a Group Policy on the server as well. The policy we’re looking for is called “Do not allow supported Plug and Play device redirection” and is located here in the tree:
- Computer Configuration
- Administrative Templates
- Windows Components
- Remote Desktop Services
- Remote Desktop Session Host
- Device and Resource Redirection
- Remote Desktop Session Host
- Remote Desktop Services
- Windows Components
- Administrative Templates
The naming of this policy is very confusing since it is enabled by default if left unconfigured. We’ll need to set the policy to “Disabled” and then reboot the computer.
Using the Yubikey Remotely
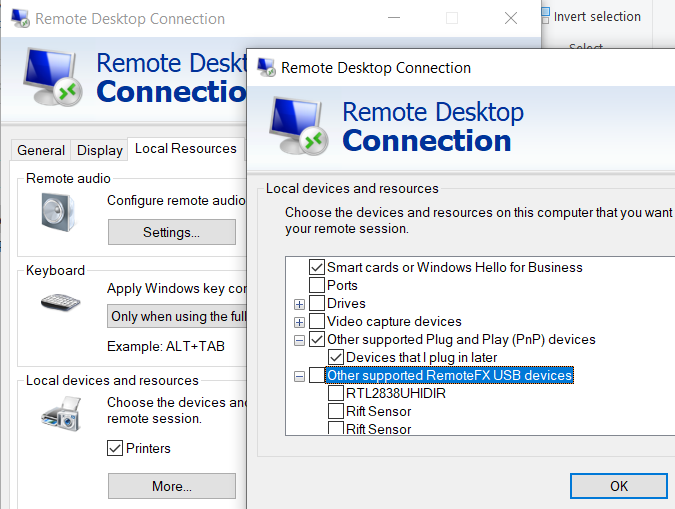 Once we’ve done all of the setup the only thing left to do is to start a remote desktop session with device redirection enabled. Go to the “Local Resources” tab of the RDP client settings and click “More…” under “Local devices and resources”. You should now see “Other supported RemoteFX USB devices” with a list of devices. Check the appropriate device and it will be available to you on the remote machine to authenticate with.
Once we’ve done all of the setup the only thing left to do is to start a remote desktop session with device redirection enabled. Go to the “Local Resources” tab of the RDP client settings and click “More…” under “Local devices and resources”. You should now see “Other supported RemoteFX USB devices” with a list of devices. Check the appropriate device and it will be available to you on the remote machine to authenticate with.
Potential Issues
If you are using the native smartcard functionality of your Yubikey (PIV or GPG) then those functions will not work while the device is being redirected via RemoteFX. You will have to use the device redirection icon on the connection bar at the top of the screen to switch back and forth between functions.
